Managed Security Operation Center (SOC) for SMBs
Managed Security Operation Center (SOC) for SMBs
With Protechs Managed SOC Services, powered by World class RocketCyber Threat Monitoring Platform, We can stop cyberattacks in their tracks. Built-in 24/7 threat monitoring enables rapid detection and response of threats, backed by a world-class security operations center.
24/7 Security Managed by a Team of Cybersecurity Experts
24/7 Security Managed by a Team of Cybersecurity Experts
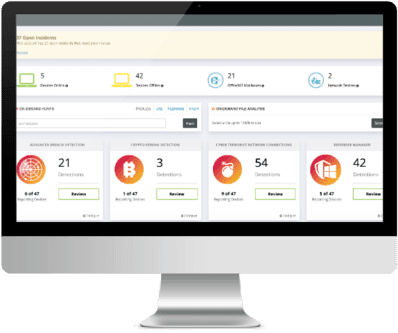
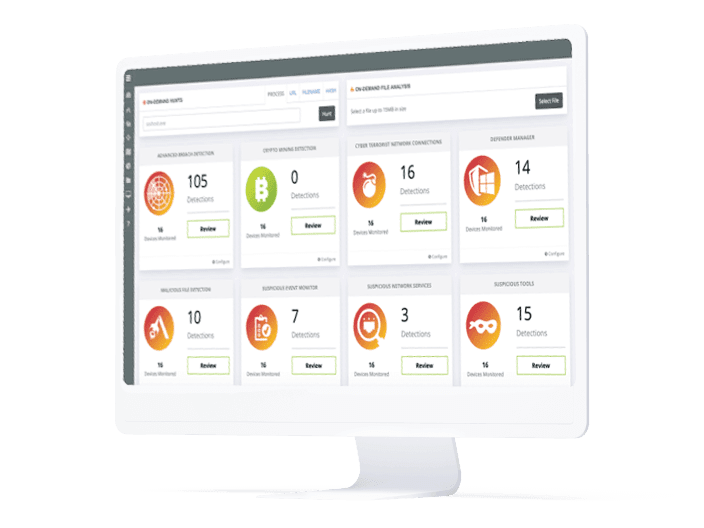
Managed SOC is a managed detection and response service. By leveraging RocketCyber’s Threat Monitoring Platform, Protechs Managed SOC Service detects suspicious activity across endpoints, networks and cloud environments. Our team of cybersecurity veterans hunt, triage and work with your team when actionable threats are discovered.

Continuous Monitoring
Continuous Monitoring
Our SOC’s real-time threat detection enables you and team to relax knowing you have around the clock protection
World-class security stack
World-class security stack
The Threat Monitoring Platform we utilize was purpose-built to provide world class service and is backed by over 50 years of cybersecurity experience.
Breach detection
Breach detection
We Take breach detection to the next level by detecting attacks that evade traditional cyber defenses.
Threat hunting
Threat hunting
We Respond to the latest threats with our elite security analyst team that proactively hunts for malicious activity and helps you respond
We Secure and Protect Clients with Managed SOC
– No Hardware Required
We Secure and Protect Clients with Managed SOC
– No Hardware Required
Comprehensive Endpoint Security
Comprehensive Endpoint Security
Our SOC Team enables us to protect your Windows and MacOS endpoints. With built in advanced breach detection, event log monitoring and intrusion detection you can respond rapidly to an attack.
We also provide proactive threat hunting and integrations with 3rd party next-gen AV solutions to ensure a layered security approach.

Real Time Network Security
Real Time Network Security
Gain new levels of network protection
With real time threat reputation and malicious connection alerts us and we respond to network attacks quickly.
We also log monitoring for firewall and edge devices as well as managing DNS information.

Cloud Security and Monitoring
Cloud Security and Monitoring
Increase your business's security stack with our detection and response best practices to the cloud. Our Managed SOC Services enables us to monitor and respond to Microsoft 365 malicious activity.
Managed SOC Services also includes Microsoft 365 and Azure AD security event log monitoring and increases your overall Secure Score
No Hardware Required
No Hardware Required
Our SOC agent deployment couldn't be any easier, due to it being entirely cloud based.
With no required hardware we can deploy SOC agent with ease and reduce overhead by not maintaining expensive hardware.

Threat Hunting and
Intel
Threat Hunting and
Intel
We take on the latest threats with real-time threat intelligence monitoring so you don’t have to.
Pulling from multiple threat intelligence feeds, our SOC analysts utilize the largest global repository of real-time threat indicators to hunt down emerging threats.

Seamless Log
Monitoring
Seamless Log
Monitoring
Our Managed SOC Service log monitoring enables us to monitor, detect and respond to changes across endpoints, networks and cloud infrastructures.
Key log data is pulled from Windows and MacOS endpoints, network firewalls / edge devices and Microsoft 365 & Azure AD without requiring a SIEM or SIEM hardware.

Breach Detection
Breach Detection
Our Managed SOC identifies tactics, techniques and procedures used by attackers. It aligns these to MITRE ATT&CK, making breach detection and response effective, effortless and easy.

Integration with PSA ticketing
Integration with PSA ticketing
When a threat is detected our SOC analysts investigate and triage each incident. They then create detailed tickets for our PSA system
These tickets include remediation details so we can respond quickly without having to hire additional staff.

Next-Generation Malware Detection
Next-Generation Malware Detection
Taking malware detection to the next level.
As part of a multi-layered security approach we use your preferred malware prevention or ours or Microsoft Defender command and control application. This includes malicious detection of files, tools, processes and more.

Intrusion Monitoring
Intrusion Monitoring
Our Managed SOC Services includes real-time intrusion monitoring to detect threats before they cause widespread damage.
By monitoring for suspicious activity, such as accessing unauthorized services and backdoor connections, we are alerted before attacks succeed.